Aruba IAP 220 with login over Social Network
This manual includes the use of the pre-Authentication rules instead of Walled Garden. This allows to login with social networks.
Basic Setup
The setup presumes the factory default status of device, however, the modification of productive hotspots is possible too. This manual shows just the features required for the hotsptot with the external captive portal functionality. Other settings are optional.
Select Add New Network and follow the wizard.
1.WLAN Settings
Set the name for the new network and switch "Primary usage" to "Guest".
2. VLAN
Switch "Client IP assignment" to "Virtual Controller managed" and "Client VLAN assignment" to "Default".
3. Security
Select "External" for "Splash page type" and "New profile" for "Captive portal profile".
3.1. Captive portal Profile
Set the Captive portal name (eg. Socfi) and then use folowing settings:
| Type | Radius Authentication |
|---|---|
| IP or hostname | connect.socifi.com |
| URL | / |
| Port | 80 |
| Use https | Disabled |
| Captive Portal failure | Deny intenet |
| Redirect URL |
Confirm the CP profile dialog and set "WISPr" and "MAC authentication" to "Disabled"
3.2. Radius server
Select "New" for "Auth server 1" and fill in the following options:
Switch to "RADIUS"
| Name | according to region related recommendation |
|---|---|
| IP address | according to region related recommendation |
| Auth port | 1812 |
| Accounting port | 1813 |
| Shared key | socifi |
| Retype key | socifi |
| Timeout | 5 sec. |
| Retry count | 3 |
| RFC 3576 | Disabled |
| NAS IP address | |
| NAS identifer | Aruba-IAP |
| Dead time | 5 min |
| DRP IP | |
| DRP Mask | |
| DRP Gateway |
Repeat the procedure for "Auth server 2"
We recommend to use this set of RADIUS servers:
Confirm the Auth server settings, go back to Security Tab and finish the configuration with the following settings:
| Load balancing | Disabled |
|---|---|
| Reauth interval | 0 hrs. |
| Accounting | Disabled |
| Blacklisting | Disabled |
| Walled garden | |
| Disable if uplink type is | (unchecked all) |
| Encryption | Disabled |
The "Walled garden" setting is suitable only for the firmware version older than 6.4.2.3-4.1.1.4_49446. It is limited by only 16 whitelist entries. The Role-based Access Rules are preffered to use in the later firmware versions and allow to use a Social Network login.
4. Access
Set "Access Rules" to "Role-based" on the Access Tab.
Select Role according to configured SSID. Open the Acces Rule editation. Change the rule settings to "Access control - Network - any - Allow - to all destinations". This Role can contain just this one rule. Delete the other rules.
In the "Role Assignment Rules" field set the edited rule as default.
In the "Roles" field create a new preauthentication rules set. Choose the name like pre-
The first rule is the external Captive Portal redirection:
Add rules for each FQDN from the Walled Garden list. "Access control - Network - Allow - to domain name" and enter the FQDN.
If you are customer with White Label solution, please add your custom domain (for example mycustomdomain.com) to the Walled Garden list.
socifi.com facebook.com akamaihd.net akamai.net edgecastcdn.net twitter.com twimg.com fastly.net li-cdn.net cloudfront.net fbcdn.net instagram.com cdninstagram.com linkedin.com licdn.com
Set this role set as "pre-authentization role" by checking this option on the Acces Tab.
Where is MAC for the SOCIFI Dashboard?
Select the network name on the default screen. The list of the all included APs will show. All these APs is neccesary to add to the SOCIFI Dashboard as unique hotspots.
The name of AP is editable. DO NOT change the name of the AP if it is used with SOCIFI. Changing the name will cause a dysfunction.
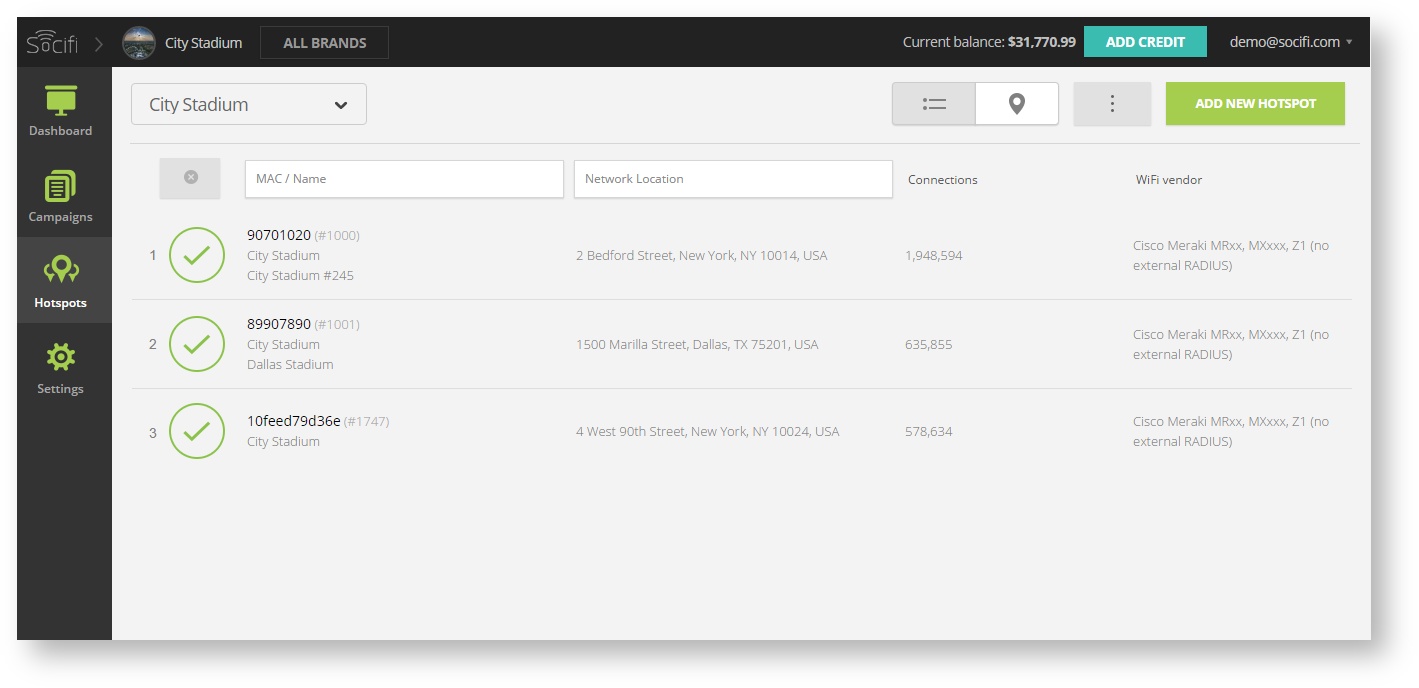
Add a new hotspot to SOCIFI Dashboard
Step 1: Login to SOCIFI Dashboard
Step 2: Click on the "Hotspots" tab on the left sidebar
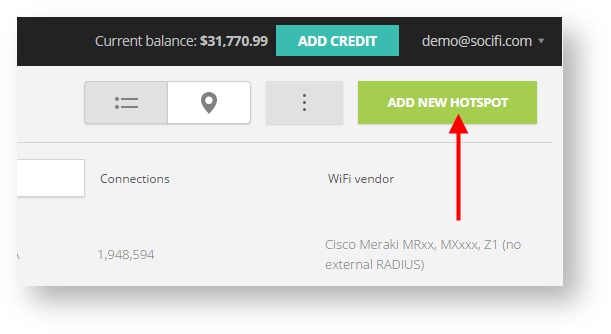
Step 3: Click on the “Add a new hotspot” button located on the top right corner on the screen (pictured below)
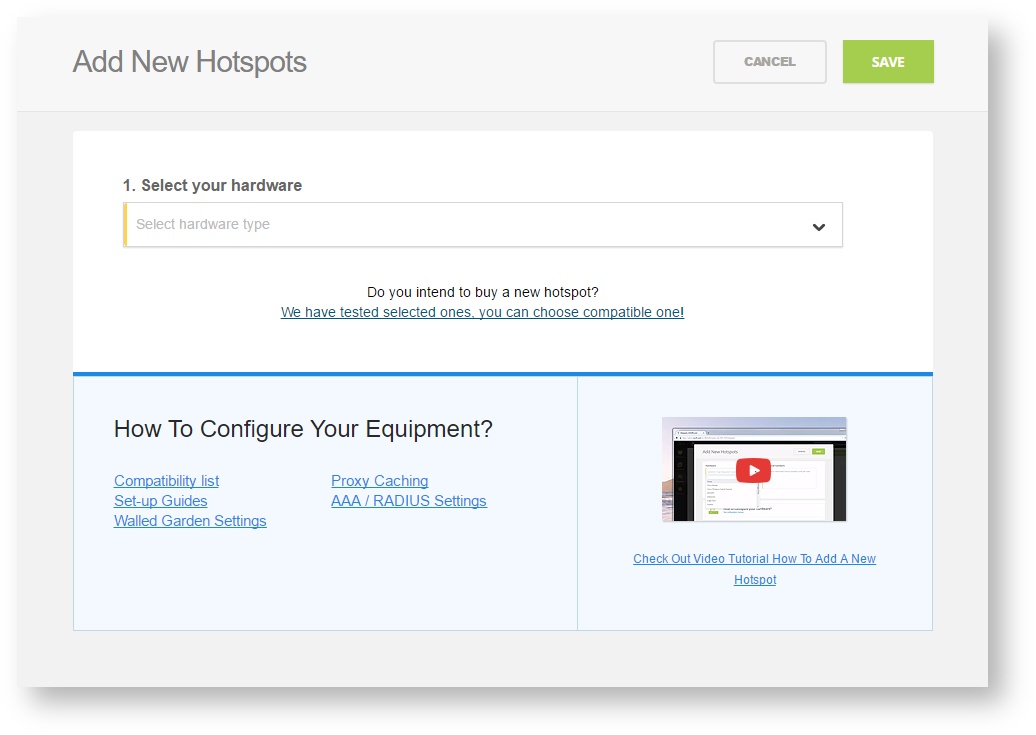
Note: A pop-up window will appear (below)
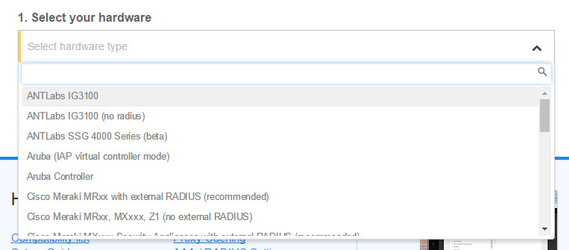
Step 4: Select the Wi-Fi hardware manufacturer from the drop down menu
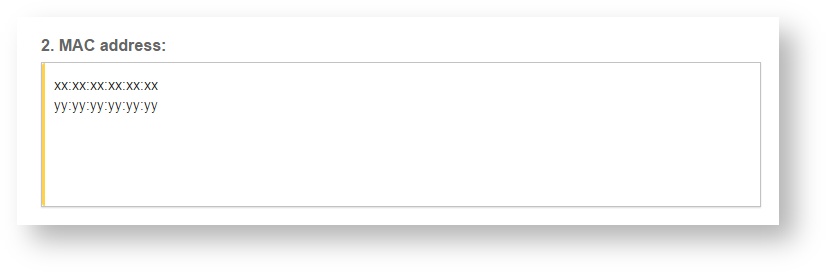
Step 5: Enter the serial number or MAC address (depending on the specific equipment manual) of your equipment. You can add multiple hotspots at once.
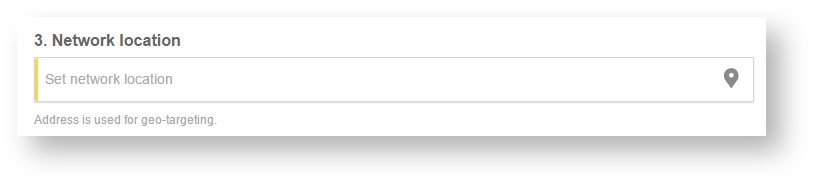
Step 6: Set your Network location (this step is essential for correct ad targeting)
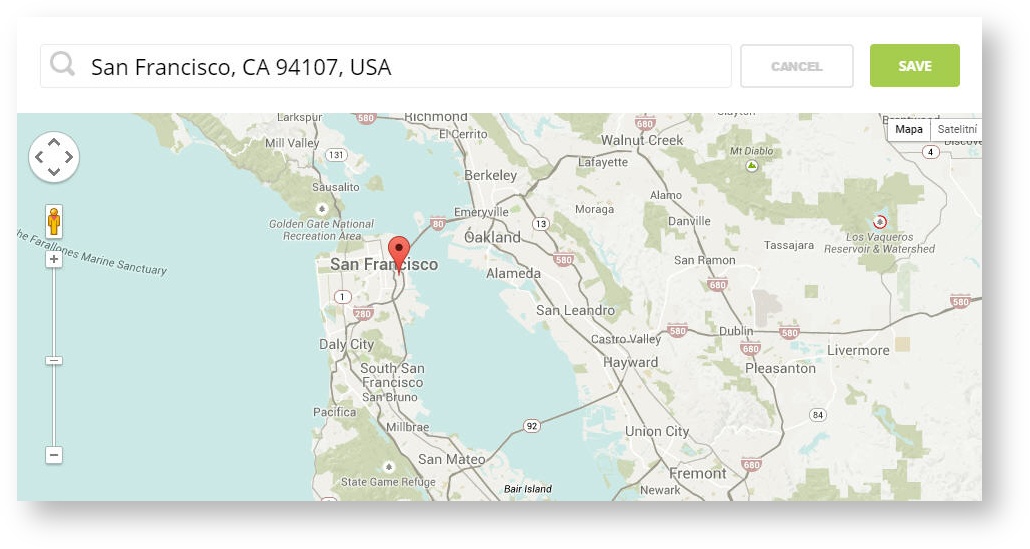
Step 7: In the pop-up window type your location or just move the marker on the map and click on the save button to confirm the selection. This address is used for ad GEO targeting.
Step 7: Click Save
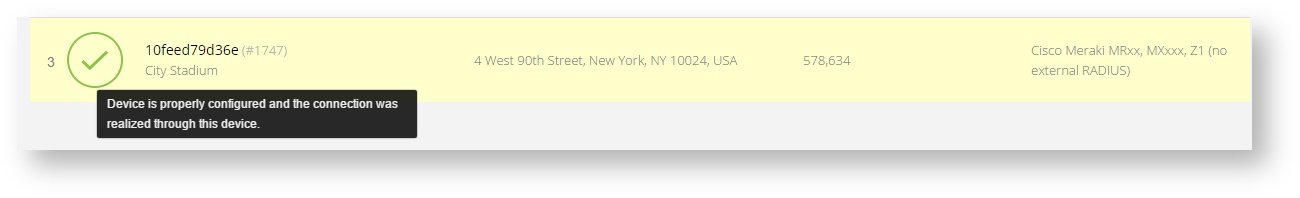
Note: Newly added hotspot are marked as (Hotspot pending). After the first user connects to the hotspot via SOCIFI, the status will automatically change and appear as (Active) within an hour. Get your first connections to test if it works properly.
Firmware version
This setup was tested on firmware verion 6.4.2.3-4.1.1.4_49446 (Build time 2015-04-05 01:53:10 PDT) and device IAP-205