Huawei AC6005 New
The setup was tested using the following devices and FW revisions:
| No. | Model Number | QTY | Software Version |
|---|---|---|---|
| 1 | AC6005 | 1 | V200R019C00SPC500 |
| 2 | Air Engine 5760-10 | 2 | V200R019C00SPC500 |
Prerequisite steps:
- Configure network interworking.
- Configure the AC and SwitchB to assign IP addresses to APs and STAs, respectively.
- Configure APs to go online.
- Configure WLAN service parameters.
Notice
Follow Huawei documentation for the configuration of Basic networking and Wireless services configuration on WLAN controller.
1. Configure external Portal RADIUS authentication on the AC
We recommend to use this set of RADIUS servers:
radius-server template SOCIFIWifi radius-server shared-key cipher <password> radius-server authentication 52.209.184.212 1812 weight 80 radius-server authentication 52.50.155.202 1812 weight 80 radius-server accounting 52.209.184.212 1813 weight 80 radius-server accounting 52.50.155.202 1813 weight 80 radius-server template default radius-server shared-key cipher <password> radius-server ip-address 52.209.184.212 shared-key cipher <password> radius-server ip-address 52.50.155.202 shared-key cipher <password> radius-server authorization 52.209.184.212 shared-key cipher <password> radius-server authorization 52.50.155.202 shared-key cipher <password>
2. Create an AAA scheme and set the authentication method to RADIUS.
aaa authentication-scheme Agile authentication-mode radius authentication-scheme SOCIFIWifi authentication-mode radius authentication-scheme default authentication-scheme radius authentication-mode radius authorization-scheme default authorization-scheme portal authorization-mode none accounting-scheme Agile accounting-mode radius accounting realtime 15 accounting-scheme SOCIFIWifi accounting-mode radius accounting realtime 3 accounting-scheme default domain default authentication-scheme Agile accounting-scheme Agile radius-server Agile domain default_admin authentication-scheme default
3. Configure a Portal server profile
http secure-server ssl-policy default_policy
http server enable
portal https-redirect enable
portal web-authen-server https ssl-policy default_policy port 8443
portal local-server ip 192.168.10.1
portal local-server redirect-url enable
url-template name urlTemplate_SOCIFIWifi
url https://connect.socifi.com
parameter start-mark #
url-parameter ap-ip AC-IP ap-mac AC-MAC redirect-url redirect-url user-ipaddress user-ip user-mac user-mac device-ip device-ip device-mac device-mac ap-name ap-name ssid ssid login-url switch_url https://192.168.2.250:8445/login
url-parameter mac-address format delimiter - normal
#
web-auth-server SOCIFIWifi
server-ip
port 443
shared-key cipher %^%#5@cw9v4y`*rP&kP=.p'7`[/{B`,Yn&k8Cs*;8]pH%^%#
url-template urlTemplate_WAASWifi
protocol http
http get-method enable
portal-access-profile name portal_access_profile
web-auth-server SOCIFIWifi direct
free-rule-template name SOCIFIWifi
free-rule acl 6031
#
free-rule-template name default_free_rule
free-rule 1 destination ip 8.8.8.8 mask 255.255.255.0
4. Configure a Walledgarden and passthrough-Domain
Enter following Walled garden ranges:
If you are a customer with the White Label solution, please add your custom domain (for example *.mycustomdomain.com) to the Walled Garden list.
*.socifi.com *.facebook.com *.akamaihd.net *.akamai.net *.edgecastcdn.net twitter.com *.twitter.com *.twimg.com *.fastly.net *.li-cdn.net *.cloudfront.net facebook.com *.fbcdn.net *.instagram.com *.cdninstagram.com instagram.com *.linkedin.com *.licdn.com linkedin.com
facebook.com and twitter.com (Yes, twice. Once with and once without the asterisk)
Pages related to Walled Garden issues
#Captive Portal domain passthrough-domain name socifi.com id 1 #Twitter Login domain passthrough-domain name *.twitter.com id 3 passthrough-domain name *.edgecastcdn.net id 4 passthrough-domain name *.twimg.com id 5 #Google Login domain Optional passthrough-domain name *.google.com id 10 passthrough-domain name *.gmail.com id 11 passthrough-domain name *.gstatic.com id 26 passthrough-domain name accounts.youtube.com id 27 #Facebook Login domain passthrough-domain name *.facebook.com id 35 passthrough-domain name *.fbcdn.net id 36 passthrough-domain name atdmt.com id 8 passthrough-domain name fbsbx.com id 9 passthrough-domain name *.akamaihd.net id 2 #Linkedin Login passthrough-domain name *.linkedin.com id 28 passthrough-domain name *.licdn.com id 29 acl name SOCIFIWifi-walledgarden 6031 rule 1 permit ip destination passthrough-domain socifi.com rule 2 permit ip destination passthrough-domain akamaihd.net rule 3 permit ip destination passthrough-domain *.edgecastcdn.net rule 4 permit ip destination passthrough-domain *.facebook.com rule 5 permit ip destination passthrough-domain *.fbcdn.net rule 6 permit ip destination passthrough-domain *.twitter.com rule 7 permit ip destination passthrough-domain *.twimg.com rule 8 permit ip destination passthrough-domain atdmt.com rule 9 permit ip destination passthrough-domain fbsbx.com rule 10 permit ip destination passthrough-domain *.gmail.com rule 11 permit ip destination passthrough-domain 21 rule 12 permit ip destination 192.168.2.0 0.0.0.255 rule 13 permit udp destination-port eq dns rule 14 permit ip destination passthrough-domain *.google.com rule 15 permit ip destination passthrough-domain cloudfront.net rule 18 permit ip destination passthrough-domain *.gstatic.com rule 22 permit ip destination passthrough-domain accounts.youtube.com
5. Register your hotspot
Step 1: Login to SOCIFI Dashboard
Step 2: Click on the "Hotspots" tab on the left sidebar
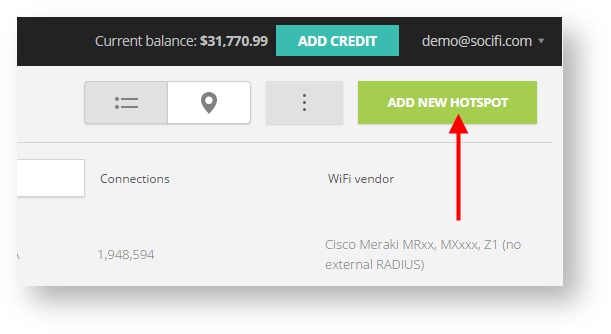
Step 3: Click on the “Add a new hotspot” button located on the top right corner on the screen (pictured below)
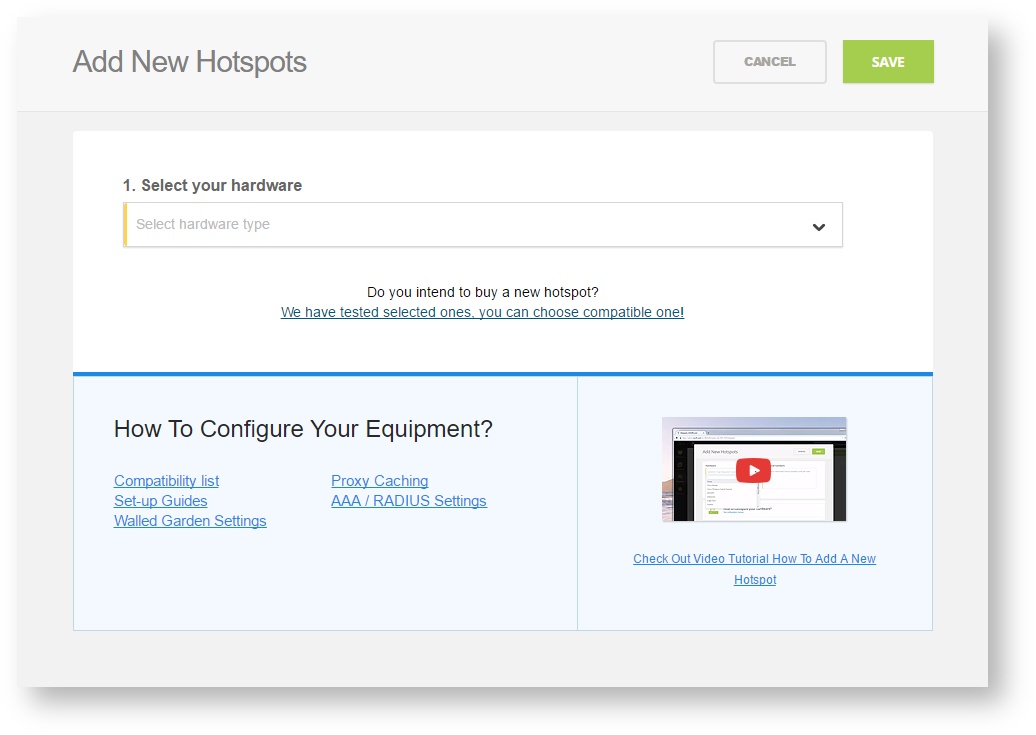
Note: A pop-up window will appear (below)
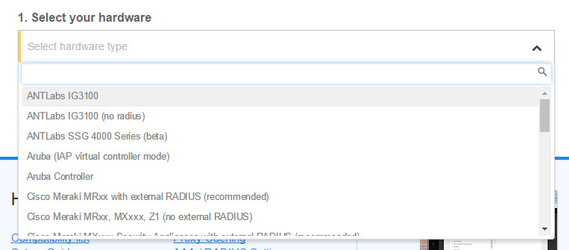
Step 4: Select the Wi-Fi hardware manufacturer from the drop down menu
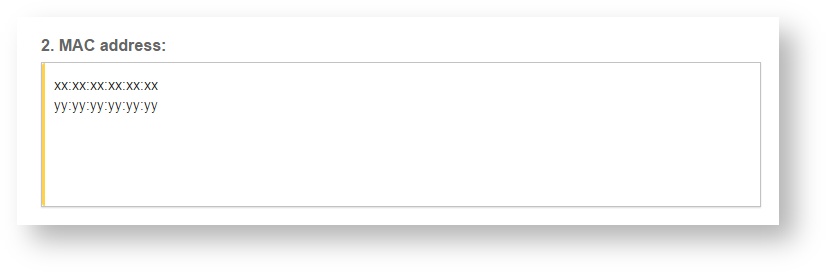
Step 5: Enter the serial number or MAC address (depending on the specific equipment manual) of your equipment. You can add multiple hotspots at once.
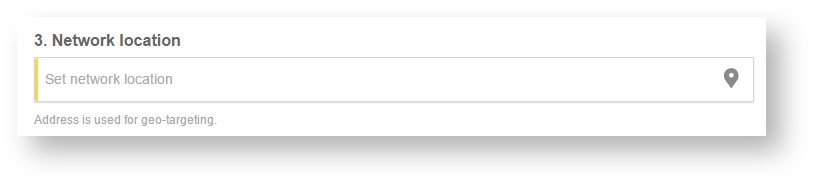
Step 6: Set your Network location (this step is essential for correct ad targeting)
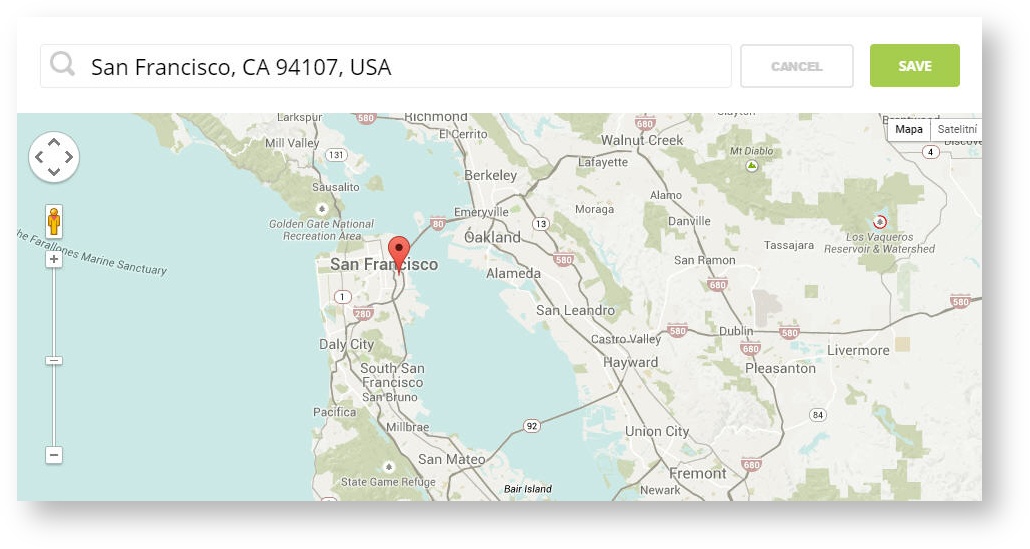
Step 7: In the pop-up window type your location or just move the marker on the map and click on the save button to confirm the selection. This address is used for ad GEO targeting.
Step 7: Click Save
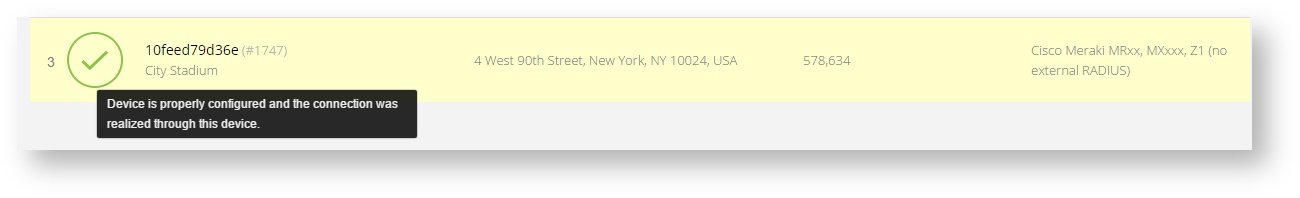
Note: Newly added hotspot are marked as (Hotspot pending). After the first user connects to the hotspot via SOCIFI, the status will automatically change and appear as (Active) within an hour. Get your first connections to test if it works properly.