Huawei AC6005
The compatibility of the Huawei controller with the SOCIFI platform was tested on the controller AC6005-8-PWR with two type of wifi AP devices (AP5010DN-AGN and AP6010DN-AGN). The version of tested firmware was AC6005V200R007C10SPC300.
Prior to starting of SOCIFI system configuration, the basic services (as VLAN subnet, DHCP, DNS, NTP ...etc) shall be set. This setup guide describes only the part of settings for the SOCIFI platform.
Security ACL - DNS-based WalledGarden
Enter following Walled garden ranges:
If you are a customer with the White Label solution, please add your custom domain (for example *.mycustomdomain.com) to the Walled Garden list.
*.socifi.com *.facebook.com *.akamaihd.net *.akamai.net *.edgecastcdn.net twitter.com *.twitter.com *.twimg.com *.fastly.net *.li-cdn.net *.cloudfront.net facebook.com *.fbcdn.net *.instagram.com *.cdninstagram.com instagram.com *.linkedin.com *.licdn.com linkedin.com
facebook.com and twitter.com (Yes, twice. Once with and once without the asterisk)
Pages related to Walled Garden issues
In the Security / ACL / Domain Name Configuration menu is necessary to create the records with the WalledGarden DNS names using the list and description above.
The next step is creating User ACL with the WalledGarden DNS records. This can be made in the Security / ACL / User ACL Settings menu. Create a User ACL and add the rule for each WalledGarden DNS records based on TCP protocol, Action Permit. It is recommended to add the rule for enabling the ICMP protocol.
For example the User ACL with its rules:
The settings detail of the Rule ID = 2. In the Dest domain is set the record from the ACL - Domain Name Configuration
AAA - Radius settings
We recommend to use this set of RADIUS servers:
For the RADIUS settings in the Security / AAA / RADIUS must be created the RADIUS Server Profile (f.e. SOCIFI_radius_server). Create records for Authentication and Accounting server in this profile. The settings are different only in the Port Number value. For the Authentication server the port 1812 shall be set. For the Accounting server the port 1813 shall be set. The secret Key ("socifi") is the same for both settings. The IP addresses of these servers are listed above.
Details of Authentication/Accounting settings
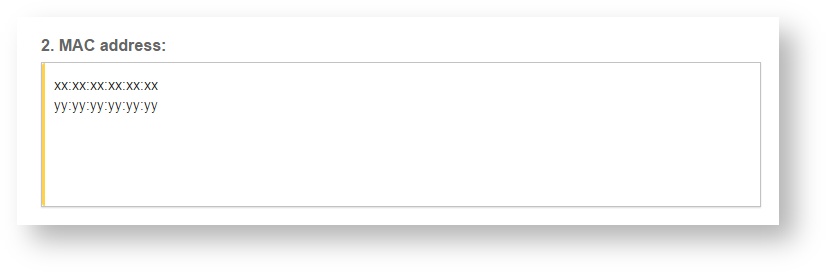
ID device - MAC address of the controller
SOCIFI uses MAC address of the controller as the identification code. You can found the MAC address in the Monitoring / AC menu under AC Basic Information.
External portal
Under the Security / AAA / External Portal Server menu create the external portal with these settings:
| Server IP | 52.251.110.178 52.51.203.246 54.232.124.137 52.44.151.156 |
|---|---|
| URL | http://connect.socifi.com |
| URL Option Settings | |
| AC-IP | AC-IP |
| User access URL | redirect-url |
| User IP | user-ip |
| AP-IP | AP-IP |
| AC-MAC | AC-MAC |
| User MAC | user-mac |
| System name | <HUW_xxxxxxxxxxxx> |
| AP-MAC | AP-MAC |
| MAC address format | normal |
| Separator | : (colon) |
Note: The value of the System name consists of string "HUW_" and MAC address of controller (see above) without delimiters (e.g. mac address of controller is "8038-bc1a-c0df" then value of System name is "HUW_8038bc1ac0df")
Authentication profile
In the Security / AAA / Authentication Profile menu shall be created separate Authentication Profile "SOCIFI_auth_profile" with following settings:
... Potal Profile ... create a new profile "SOCIFI_portal_access_profile" with the Active server properties set to "SOCIFI" (see above to the External Portal settings)
... Authentication-free Rule ... create a new profile "SOCIFI_free_rule" and set the control mode to the ACL value. ACL number is the number of the User ACL rule with the DNS Walled Garden rule (see above to the Security ACL - DNS-based WalledGarden settings)
... Radius Server Profile ... select the "SOCIFI_radius_servers" as the RADIUS Server Profile
... finally, select the value "radius" as Authentication Scheme with the First authentication set on the RADIUS authentication property.
Profile management
In the AP / Profile menu bind required SSID and the wifi properties with the SOCIFI external portal authentication properties. The SSID and the wifi properties are generally set according to user needs.
For SOCIFI system are important only authentication properties settings. Create the SOCIFI_VAP_profile in the VAP Profile properties.
Under Authentication Profile select SOCIFI_auth_profile.
Finally select the "SOCIFI_VAP_Profile" for any AP group where the SOCIFI system use is intended.
Connecting your Huawei controller to SOCIFI Dashboard
When adding Huawei device into SOCIFI Dashboard, use the MAC address of the controller as described in the part of ID device - MAC address of controller
Step 1: Login to SOCIFI Dashboard
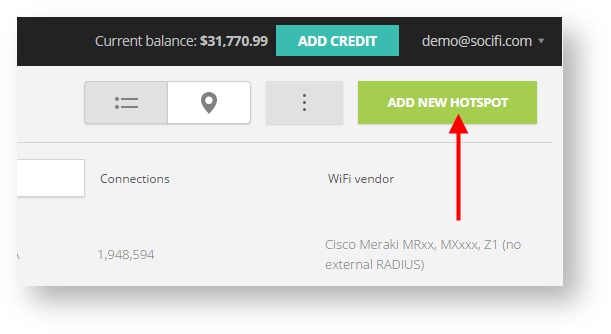
Step 2: Click on the "Hotspots" tab on the left sidebar
Step 3: Click on the “Add a new hotspot” button located on the top right corner on the screen (pictured below)
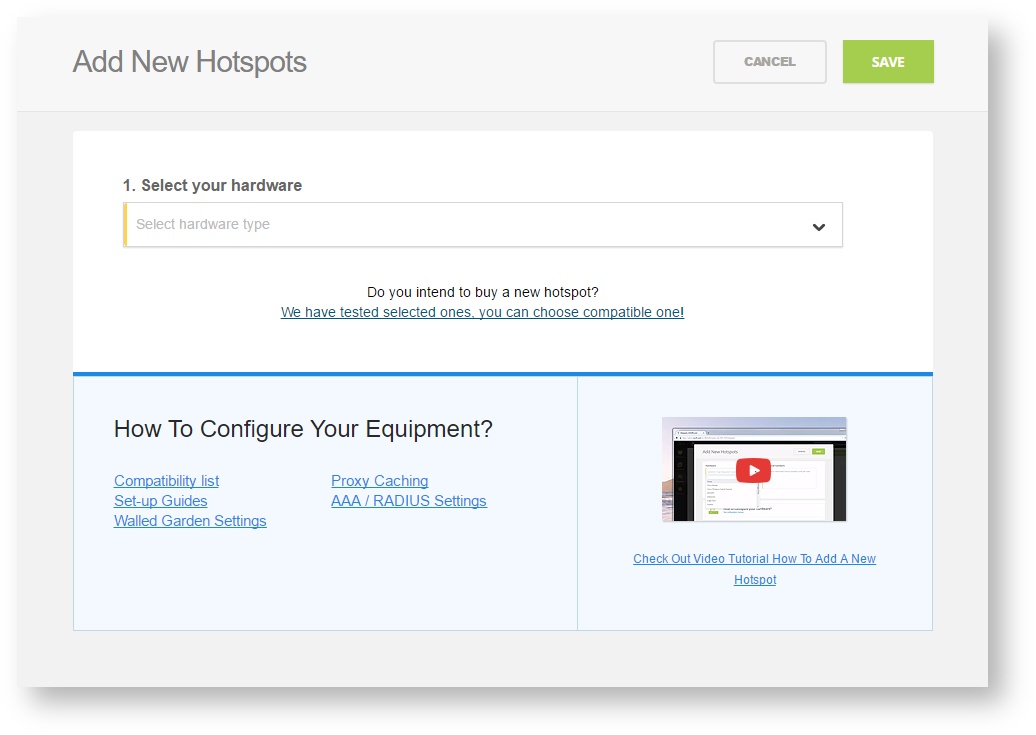
Note: A pop-up window will appear (below)
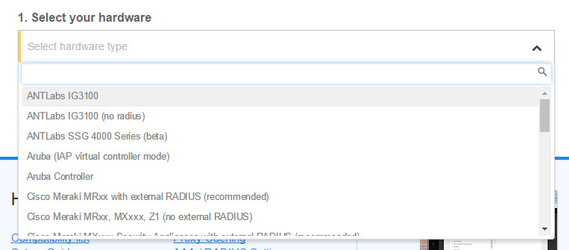
Step 4: Select the Wi-Fi hardware manufacturer from the drop down menu
Step 5: Enter the serial number or MAC address (depending on the specific equipment manual) of your equipment. You can add multiple hotspots at once.
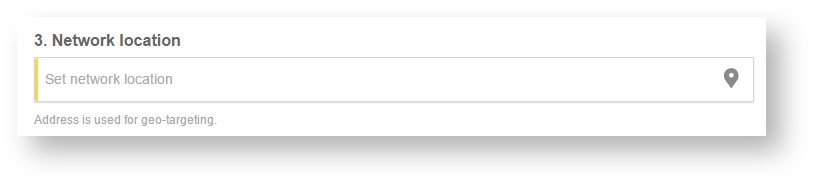
Step 6: Set your Network location (this step is essential for correct ad targeting)
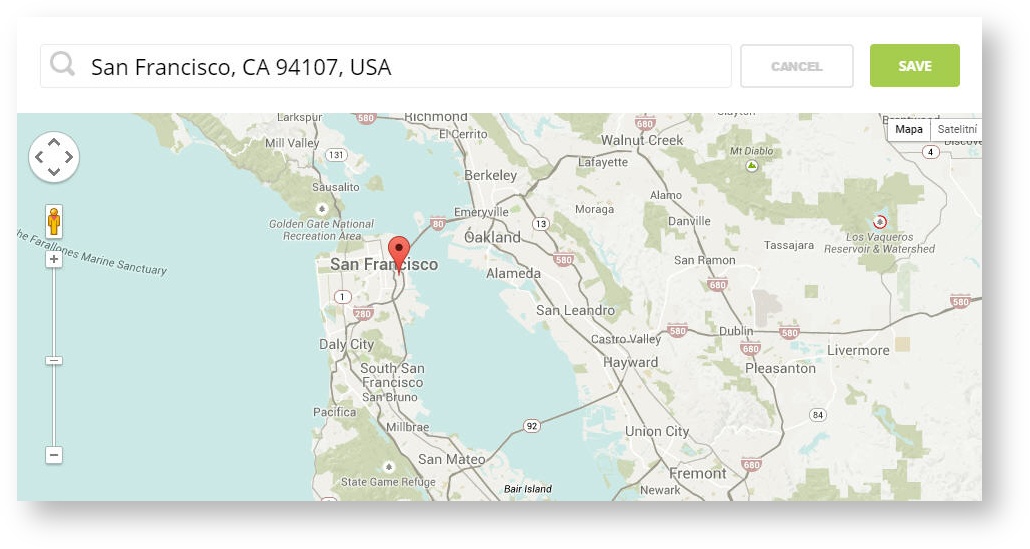
Step 7: In the pop-up window type your location or just move the marker on the map and click on the save button to confirm the selection. This address is used for ad GEO targeting.
Step 7: Click Save
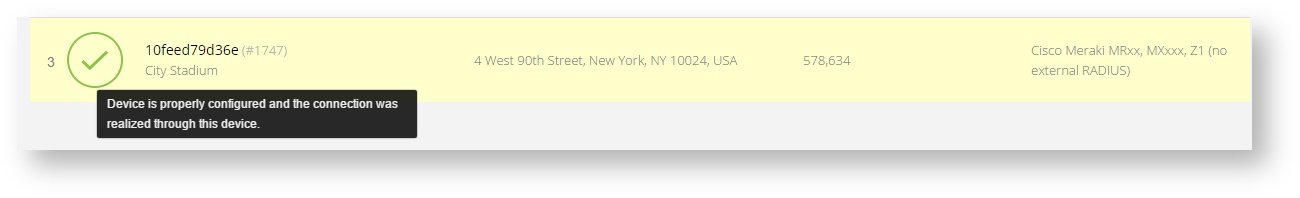
Note: Newly added hotspot are marked as (Hotspot pending). After the first user connects to the hotspot via SOCIFI, the status will automatically change and appear as (Active) within an hour. Get your first connections to test if it works properly.
Please pay attention to these important settings:
the value of the variable System name - "HUW_<mac_of_the_controller_without_delimiters>" in the External Portal settings
- time synchronization
- DNS WalledGarden - used WhiteLabel domain shall be added to the WalledGarden.
- the correct Server IP in the External Portal settings - There are usually set IPs of SOCIFI servers for the backward authentication communication by UDP protocol. If the controller is located in the local LAN without direct public IP address, wrong recognition of UDP communication source may occurs. In this case, the local IP of NAT service should be listed. For the best detection use CLI with the following commands: "terminal monitor", "terminal debugging" and "debugging the web all".
- open the UDP communication with the destination port 2000 (on the controller side) on all firewalls or ACLs between the Huawei controller and the SOCIFI servers on the internet.